15.07.2025
MAC Address Rotation Is Here: What’s Next for Guest Identification in Hospitality
With iOS 18, Apple introduced MAC address rotation, disrupting how hotels identify returning guests on Wi-Fi. This article explores what’s replacing MAC-based recognition and how the hospitality industry is adapting.
For years, guest identification in hospitality Wi-Fi has depended on MAC addresses. They enabled automatic recognition of returning guests, session tracking, and frictionless whitelisting.
But that era is coming to an end.
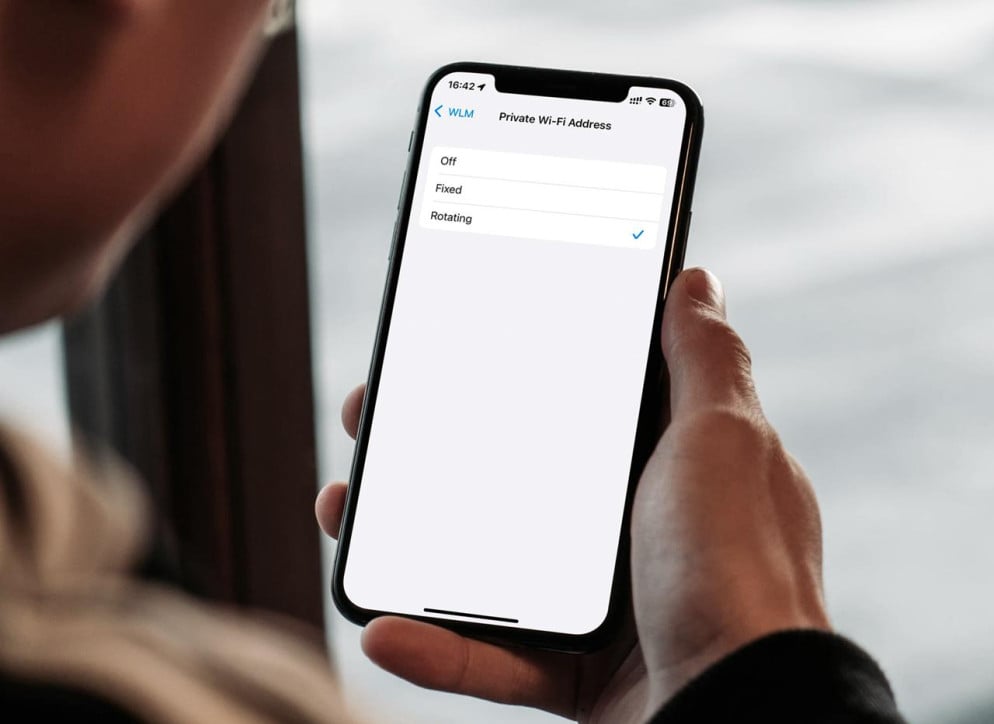
With the release of iOS 18 in September 2024, Apple introduced MAC address rotation: when enabled, a device changes its MAC address every two weeks. Android has had similar features for some time.
Based on our experience, this shift has already begun to impact how hotels manage Wi-Fi authentication and personalization.
What It Means in Practice
- MAC-based recognition is no longer reliable beyond 14 days.
- Features such as "Welcome Back," auto-login, and device-specific access are not functioning correctly.
- Our clients report increasing cases where loyal guests are treated as “new” users on each visit.
- We're losing a simple way to connect a guest with a specific device — and that impacts the guest experience.
At the same time, we see this as a signal: it’s time to move away from passive identification and toward explicit, consent-based models.
Why this matters for guest loyalty
When a guest’s device is no longer recognised via its MAC address, hotels lose not just connectivity convenience — they also lose powerful touchpoints for personalising the stay. Imagine a returning guest who normally gets a “Welcome back!” message, a preferred room temperature, or tailored upsell offers — all that becomes harder when the system treats them as new.
That’s why shifting to consent-based identification (SSO, loyalty credentials) isn’t just a tech upgrade — it’s a competitive advantage for guest engagement and retention.
What We Practice Instead
We've been working with several approaches that don't rely on MAC addresses — and they’re showing promise in live hotel environments.
1. Passpoint / Hotspot 2.0
In theory, this allows seamless reconnection. But in practice:
- Guests must install a certificate, which triggers system warnings.
- Device compatibility varies;
- Requires centralized network control, which few hotels have.
Our clients who have tried it usually end up limiting its use to a few VIP use cases or internal staff networks.
2. Dynamic PPSK (Private Pre-Shared Key)
Each guest gets a unique Wi-Fi password. We’ve tested this with several hotels. It’s secure, but:
- Doesn’t support captive portals, which are needed for legal compliance;
- Not fully compatible with WPA3 or 6GHz networks;
- Hard to manage across multiple properties.
Currently, we view this as a niche solution, rather than a general replacement.
3. SSO with Loyalty Integration
This is where we see the most traction.
Guests log in using loyalty credentials. It’s familiar, secure, and offers:
- Consent-based identification;
- Clear value exchange (points, perks, personalized offers);
- Integration with existing guest data.
From our experience, this is where the industry is headed — and where we see the best ROI.
4. Phone Number and Email Authentication
Still relevant. Still effective. We use this as a fallback method when SSO is unavailable.
It’s not new, but it works — and guests understand it.
What I See Happening in the Market
Vendors are adjusting. A good example is Apple’s new AirPlay setup for hotels.
Guests scan a QR code on the TV to connect to Wi-Fi, review the terms of service, and explicitly give consent: no app, no login portal — just one step.
This is a glimpse of how the industry might evolve: less friction, more clarity, and consent at the center of the process.
Final Thoughts
Guest identification is changing. MAC addresses are no longer reliable. From our work with hotels across different regions, we see a clear trend: implicit tracking is being replaced with explicit, guest-approved methods.
It’s not just about compliance it’s about adapting to real guest expectations.
Want to see how this works in practice?
Book a demo and we’ll show you how we help hotels move beyond MAC-based identification with minimal disruption.